Investigating WinRAR Code Execution Vulnerability (CVE-2018-20250) at Internet Scale
Authors: lywang, dannywei
0x00 Background
As one of the most popular archiving software, WinRAR supports compress and decompress of multiple file archive formats. Check Point security researcher Nadav Grossman recently discovered a series of security vulnerabilities he found in WinRAR, with most powerful one being a remote code execution vulnerability in ACE archive decompression module (CVE-2018-20250).
To support decompression of ACE archives, WinRAR integrated a 19-year-old dynamic link library unacev2.dll, which never updated since 2006, nor does it enable any kind of exploit mitigation technologies. Nadav Grossman uncovered a dictionary traversal bug in unacev2.dll, which could allow an attacker to execute arbitrary code or leak Net-NTLM hashes.
0x01 Description
ACE archive decompression module unacev2.dll fails to properly filter relative paths when validating target path. Attacker can trick the program to directly use a relative path as target path. By placing malicious executable in system startup folder, it can lead to arbitrary code execution.
0x02 Root Cause
unacev2.dll validates destination path before extracting files from ACE archives. It gets file_relative_path from archive file and use GetDevicePathLen(file_relative_path) to validate the path. The path concatenation is performed according to return value of the function, as shown in following diagram:
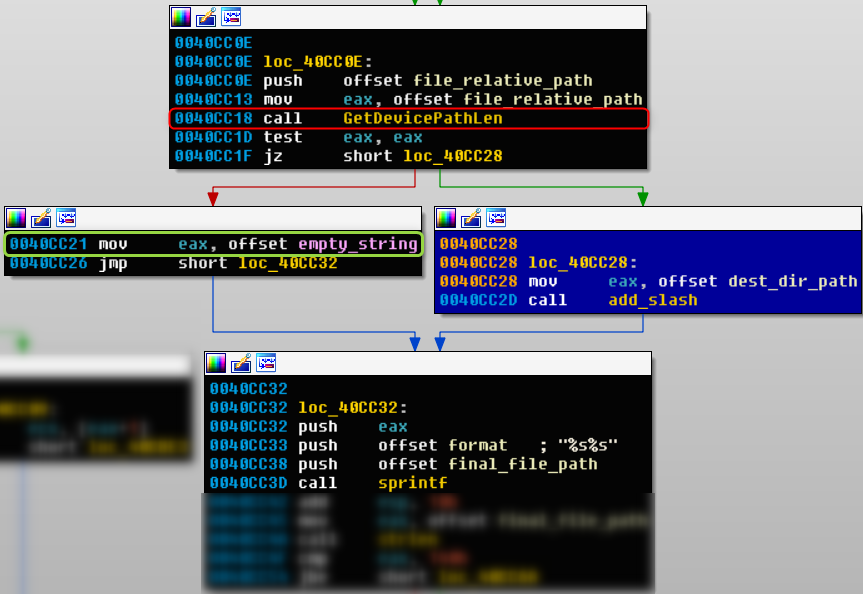
When GetDevicePathLen(file_relative_path) returns 0, it will concatenate target path with relative path in archive to form a final path:
1 | sprintf(final_file_path, "%s%s", destination_folder, file_relative_path); |
Otherwise, it directly uses relative path as the final path:
1 | sprintf(final_file_path, "%s%s", "", file_relative_path); |
if an attacker can craft a malicious relative path that can bypass multiple filter and validation functions such as StateCallbackProc(), unacev2.dll!CleanPath(), and make unacev2.dll!GetDevicePathLen(file_relative_path) return a non-zero value, the malicious relative path will be used as final path for decompression.
Nadav Grossman successfully crafted two such paths:
| # | Malicious Path | Final Path |
|---|---|---|
| 1 | C:\C:\some_folder\some_file.ext | C:\some_folder\some_file.ext |
| 2 | C:\\10.10.10.10\smb_folder_name\some_folder\some_file.ext | \10.10.10.10\smb_folder_name\some_folder\some_file.ext |
Variation 1: Attacker can place a file at arbitrary path on victim’s computer.
Variation 2: Attacker can steal victim’s Net-NTLM hash. Attacker can then perform a NTLM relay attack to execute code on victim’s computer.
It is worth mentioning that WinRAR runs at normal user privilege. Therefore, an attacker cannot place a file in the common startup folder (“C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup”). Placing a file in user startup folder (“C:\Users<user name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”) requires guessing or brute-forcing a valid user name.
However, in most common scenarios, where victims download archive file to Desktop (C:\Users<user name>\Desktop) or Downloads (C:\Users<user name>\Downloads) folder then extract the archive file in-place, the working directory of WinRAR is the same as the archive file. By using directory traversal, attacker can release payload to Startup folder without guessing a user name. Nadav Grossman crafted the following path to build a remote code execution exploit:
1 | "C:../AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\some_file.exe" |
0x03 Affected Software
As a shared library, unacev2.dll is also used by other software that supports ACE file decompression. These software are also affected by this vulnerability.
Our Project A’Tuin system scans software at internet scale. We scanned through all software that used this shared library. The following diagram shows the version distribution of this library:

Project A’Tuin can also traces shared libraries back to their dependent software. We currently observe that 15 Chinese software and 24 non-Chinese software are affected.
Most of them can be categorized as utility software. Among them there are at least 9 file archivers, and 8 file explorer / commanders. Many other software seems to simply include unacev2.dll module as part of WinRAR package, for its own file decompression usage.
0x04 Mitigations
WinRAR released version 5.70 Beta 1 to patch this vulnerability. Since the vendor of unacev2.dll was out of business in August 2017 and it is a closed source product, WinRAR decided to remove ACE decompression feature from WinRAR entirely.
360Zip has also patched this vulnerability by removing unacev2.dll.
For users of other affected products, we suggest contacting the vendor for updated versions. If no updated version is available, users can temporarily work around this vulnerability by removing unacev2.dll from installation directory.
0x05 References
[1] Extracting a 19 Year Old Code Execution from WinRAR https://research.checkpoint.com/extracting-code-execution-from-winrar/
[2] ACE (compressed file format) https://en.wikipedia.org/wiki/ACE_(compressed_file_format)
