CVE-2016-1707 Chrome Address Bar URL Spoofing on IOS
Address Bar URL Spoofing on IOS Chrome (CVE-2016-1707), I report the vulnerability to Google in June 2016. Spoofing URL vulnerability can be forged a legitimate Web site address. Attacker can exploit this vulnerability to launch phishing attack.
Affected version: Chrome < v52.0.2743.82, IOS < v10
0x01 Vulnerability Details
POC:
1 | <script> |
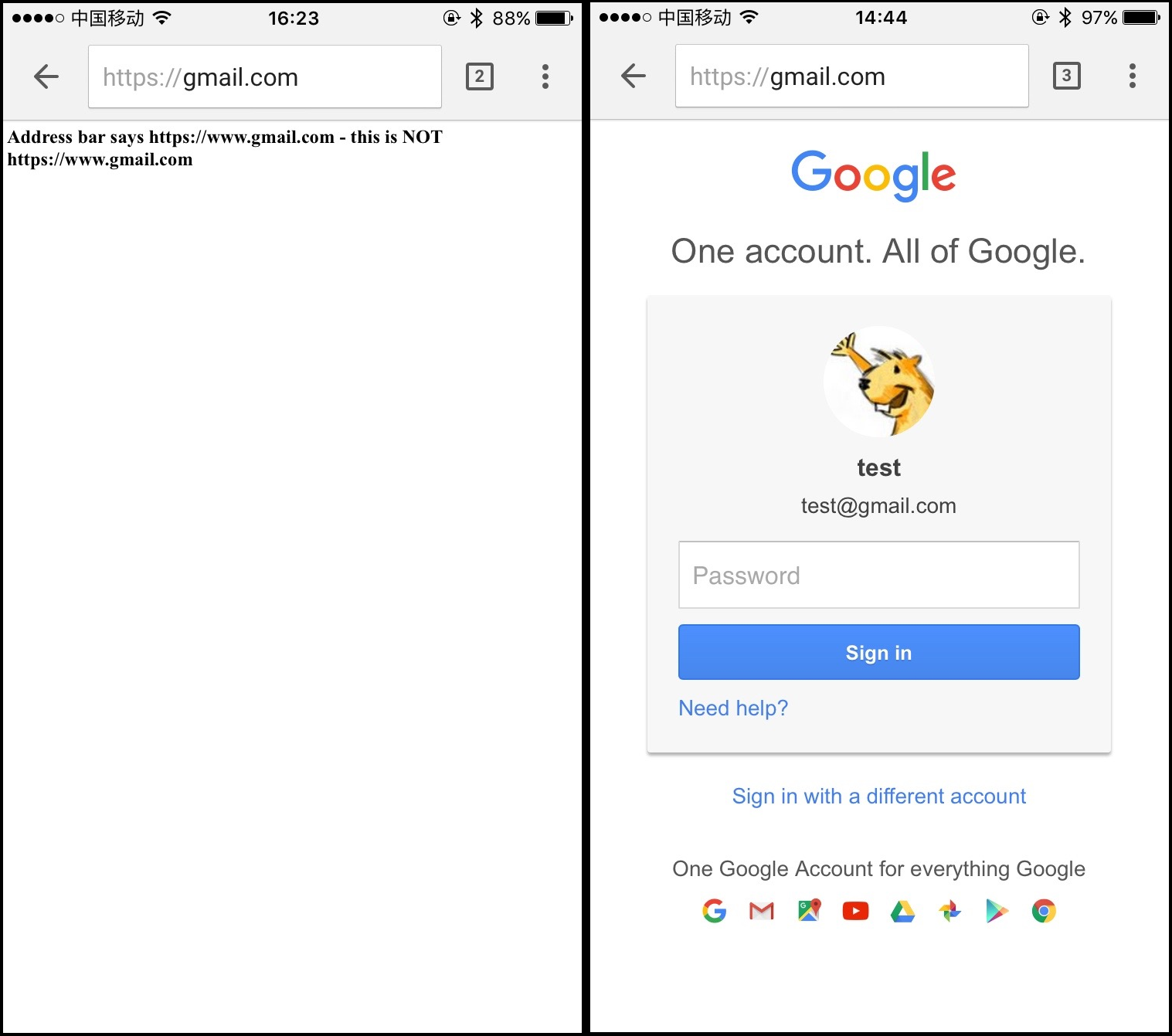
How the vulnerability happened? First click on the ‘click me’ link, The browser opens a new window called aaaa, this page loads the “https://hack.com::", this address can be casually write. Continue running Pwned () after 500 microseconds , open the ‘https://www.gmail.com' in the aaaa window, of course, this URL can be empty. Up to now, all the code is running well, and the next code is the core code to trigger the vulnerability.
base64 payload code:
1 | <body></body> |
Begin loading ‘https://gmail.com::’ in aaaa window , happying, Chrome allows to load ‘https://gmail.com::’, and then chrome address as a pending entry. Because ‘https://gmail.com::’ is an invalid address, i think Chrome should jump to about:blank, but chrome commits pending entry (‘https://gmail.com::') and promotes it as a last committed URL. At this point, the entire loading process is completed. A perfect Spoofing URL vulnerability was born.
0x02 Fixed
[IOS] Do not commit invalid URLs during web load.
[self optOutScrollsToTopForSubviews];
1 | // Ensure the URL is as expected (and already reported to the delegate). |
0x03 Discloure Timeline:
2016/6/22 Report to Google,https://bugs.chromium.org/
2016/6/22 Google assigned,Security_Severity-High
2016/7/14 Google reward $3000
2016/7/20 Google advisory disclosed,CVE-2016-1707
2016/10/2 Google allpublic disclosed
0x04 References
[1] https://googlechromereleases.blogspot.com/2016/07/stable-channel-update.html
[2] https://bugs.chromium.org/p/chromium/issues/detail?id=622183
[3] https://chromium.googlesource.com/chromium/src/+/5967e8c0fe0b1e11cc09d6c88304ec504e909fd5
