BadTunnel - A New Hope
This article purposes a new attack model to hijack TCP/IP broadcast protocol across different network segment, named “BadTunnel”.
With this method, NetBIOS Name Service Spoofing can be achieved, regardless of the attacker and the victim is on the same or different network, the firewalls and NAT devices in between. All it need is the victim navigate to a malicious web page with IE or Edge, or open a specially crafted document, and the attacker can hijack the victim’s NetBIOS name query to spoof as print server or file server in the local network.
By hijacking the WAPD name, the attacker can hijack all network communications, including but not limited to usual web accesses, Windows Update service and Microsoft Crypto API Certificate revocation list updates. Once the hijack is successful, it is easy to achieve arbitrary execution of program on the target system by using Evilgrade [1].
This method is effective on all Windows versions before the June 2016 patch, and can be exploited through all Internet Explorer, Microsoft Edge, and Microsoft Office versions, and can also be exploited through third-party applications. In fact, BadTunnel attack can be conducted on anywhere that a file URI scheme or UNC path can be embedded. For example, if a shortcut’s icon path is pointed to the malicious file URI scheme or UNC path, the BadTunnel attack can be triggered at the moment the user sees it in the Windows Explorer, which means BadTunnel can also be exploited through web pages, emails, USB flash drives and many other ways. It can even impact Web servers and SQL servers [2].
(This article does not include all contents covered by the BadTunnel research, the remaining part will be released in my presentation “BadTunnel: How do I get Big Brother power” on BlackHat US 2016.)
0x00 Background
NetBIOS is an ancient protoco. In 1987, IETF released RFC 1001 and RFC 1002, which defined NetBIOS over TCP/IP or NBT for short. NetBIOS includes three services, among them the Name service NetBIOS-NS, or NBNS for short. NBNS can resolve local names by broadcasting in the LAN.
When trying to access \\Tencent\Xuanwu\Lab\tk.txt, NBNS will send a NBNS NB query to the broadcast address:
Who is “Tencent”?
Any host in LAN can respond to this request:
“Tencent” is at 192.168.2.9.
Then the victim’s computer will accept this response and tries to access \\192.168.2.9\XuanwuLab\tk.txt.
This mechanism is definitely not safe, but since LAN is usually treated as trusted network, this spoofing possibility is not considered as vulnerability – just like the ARP Spoofing.
WPAD (Web Proxy Auto-Discovery Protocol) is another ancient protocol with over 20 years of history. As the name suggests, it is used for automatically discover and configure system proxy. Almost all operating systems support WPAD, but only Windows enable it by default. According to this protocol, Windows tries to resolve the name http://WPAD/wpad.dat to retrieve proxy configuration script.
On Windows, the name “WPAD” is resolved by NBNS. As previously stated, any host can claim it is “WPAD” in a LAN. This is not secure but acceptable since the LAN is considered trusted network environment. Although WPAD hijacking has been found more than a decade ago and used by the Flame worm, it is not considered as security vulnerability – just like the ARP Spoofing.
NBNS is implemented on top of the UDP protocol, which is a stateless protocol. Firewalls, NAT devices and other network devices cannot distinguish which session the UDP packet belongs to, so they must allow the UDP packet on both directions.
NBNS name query uses the broadcast protocol, but like most other broadcast protocols, NBNS accept responses from outside the network segment. Which means, if 192.168.2.2 sends a request to 192.168.2.255, but 10.10.10.10 responds in time, the response will be accepted by 192.168.2.2. In some enterprise networks, this is required by the network topology.
0x01 Implementation
If we could send a fake response from outside the network segment when the name query is performed by the NBNS, it can still be accepted. Therefore, NBNS Spoofing across different network segment is possible, but with a few problems:
- Most hosts have firewall enabled, which makes it impossible to send data to the host. Even if there is no firewall, there is no way to directly send data from internet to intranet. Does that mean we can only do NBNS Spoofing to these systems that have public IP address and no firewall enabled?
- There is a DNS protocol look-alike encapsulated within the NBNS protocol, so it also includes a Transaction ID. Only packets with matching Transaction IDs are accepted.
- How do we know when to send the NBNS Spoofing packet, if the host outside the LAN cannot receive the NBNS NB query broadcast?
Fortunately, all these problems can be solved.
First, the Windows operating system only uses 137/UDP port for NBNS. “Only” means that the source and target ports are always 137/UDP. If an intranet host 192.168.2.2 is sending NBNS request to 10.10.10.10, it will look like this:
192.168.2.2:137 -> NAT:54231 -> 10.10.10.10:137
The response from 10.10.10.10 will look like this:
192.168.2.2:137 <- NAT:54231 <- 10.10.10.10:137
That is, the local firewalls on 192.168.2.2 or NAT, or any other intermediate network devices, must allow any UDP packet from 10.10.10.10:137 to 192.168.2.2:137 to pass through in a certain amount of time, if it allows the query at all. This opens up a dual direction UDP tunnel, hence the name BadTunnel:
192.168.2.2:137 <-> NAT:54231 <-> 10.10.10.10:137
One quick experiment to help you understand this tunnel:
Prepare two systems with firewall enabled, with IP address set to 192.168.2.2 and 192.168.3.3, respectively.
On 192.168.2.2, execute command “nbtstat -A 192.168.3.3”, it will fail.
On 192.168.3.3, execute command “nbtstat -A 192.168.2.2”, it will success.
On 192.168.2.2, execute “nbtstat -A 192.168.3.3” once again, it will success.
How can we make 192.168.2.2 send a NBNS request to 10.10.10.10? When Windows is trying to access a file URI scheme or UNC path with IP address, if the 139 and 445 port of the target is inaccessible – either timed out or been reset– the system will send a NBNS NBSTAT query to this IP address. There are numerous ways to make a system access a file URI scheme or UNC path.
The Microsoft Edge and Internet Explorer both try to resolve the file URI scheme or UNC path in the web page:
<img src=”\\10.10.10.10\BadTunnel”>
All types of Microsoft Office documents can have embedded file URI scheme or UNC path, the same is true for many third-party document types.
If we have a shortcut with icon path point to a UNC path, this UNC path is accessed once the shortcut is shown on the screen.
If the target is a web server, maybe only one HTTP request is needed:
http://web.server/reader.aspx?ID=\\10.10.10.10\BadTunnel
The NBNS Transaction ID is not random but incremental. As we have noted previously, the NBNS sends a NBNS NB query when resolving a name; the system sends a NBNS NBSTAT query when failing to access a file URI scheme or UNC path. NBNS NB query and NBNS NBSTAT query not only uses the same 137/UDP port, but also shares the same Transaction ID counter. That is, when 192.168.2.2 fails to access \\10.10.10.10\BadTunnel, the NBNS NBSTAT query it send to 10.10.10.10 not only opens up a dual direction UDP tunnel, but also leaks the Transaction ID value to 10.10.10.10.
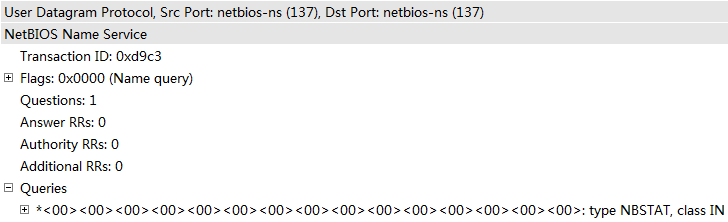
That is, a single NBNS NBSTAT query solved both problem 1 and 2. And the third problem is even easier to solve. Just like we can embed <img src=”\\10.10.10.10\BadTunnel”> in our web page, we can also embed:
<img src=”http://WPAD/wpad.dat" >
In this way, we can control the time the system sends the NBNS NB query to WPAD, so we can craft our response in time. Finally the system will cache the response to http://WPAD/wpad.dat in its web cache. Later, when the system is requesting http://WPAD/wpad.dat to set proxy configuration, it will retrieve from the web cache. At least for Windows 7, the spoofed http://WPAD/wpad.dat will persist after reboots, just like other web resources.
Even if Web cache is not in place, the NBNS has its own caching mechanism. With one successful NBNS Spoofing, the spoofed response will be cached for 10 minutes:
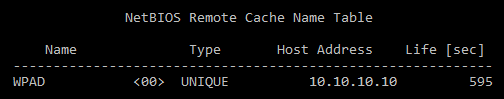
In the next 10 minutes the operating system itself will also try to resolve the WPAD name and access http://WPAD/wpad.dat to download proxy configurations, so it will get the spoofed response. Once the attacker has successfully hijacked the user’s network flow, he can periodically redirect certain HTTP requests to make the BadTunnel attack persistent:
HTTP/1.1 302 Found
Content-Type: text/html
Location: file://10.10.10.10/BadTunnel
Content-Length: 0
0x02 Conclusion
The BadTunnel attack described in this article is a serious security problem, and the root cause is not obvious to find. The following dependencies are required for the attack to be successful:
- UDP protocol is connectionless.
- Broadcast requests can accept response from outside the network segment.
- WPAD is enabled by default on Windows.
- Windows file APIs supports UNC path by default.
- When Windows fails to access a UNC path by connecting to 139 and 445 ports, a NBNS NBSTAT query will be performed.
- NBNS always uses the same port on the client and server side.
- NBNS Transaction ID uses a counter rather than a RNG.
- NBNS NBSTAT query and NBNS NB query shares the same counter.
- WPAD shares the same Web and NBNS cache with other applications in the system.
These designs do not seem to be a problem independently; some are even required. We certainly can’t blame UDP for connectionless. Even the NBNS Transaction ID is not randomly generated, this alone does not become security vulnerability. The NBNS NB mechanism was designed for the intranet, and any host in the intranet can receive the NBNS NB query broadcast packets. However, although seems not to be a problem independently, they become a massive vulnerability when work collaboratively. How can we find the next BadTunnel?
0x03 Mitigation Recommendations
Even if the MS16-063 and MS16-077 patch cannot be installed immediately, there are workarounds that can stop the BadTunnel attack.
For enterprises, they can drop the 137/UDP packets on perimeter firewalls.
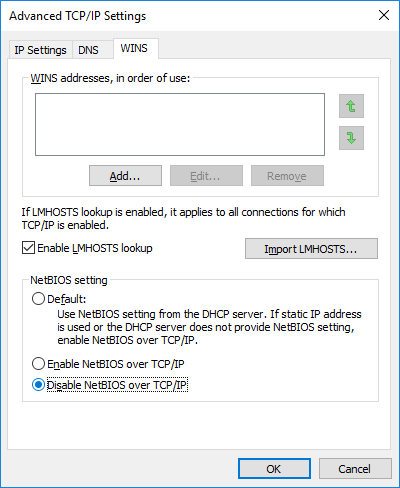
For end users that do not need to access Windows network sharing services, NetBIOS over TCP/IP can be disabled:
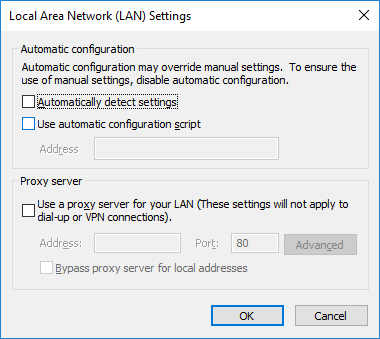
For minimal compatibility impact, WPAD address can be pinned to 127.0.0.1 in %SystemRoot%System32driversetchosts, or the automatic proxy discovery can be disabled to prevent hijacking:
However, BadTunnel is not limited to WPAD, and this does not stop hijacking of other names.
0x04 A Little Disappointment
Using BadTunnel to hijack WPAD is possibly the Windows vulnerability that has the widest impact and most exploit channels in the history. It is also the only vulnerability that can target all versions of Windows with one exploit. It could have been more interesting.
Apple’s Mac OS also implemented NetBIOS, and supports UNC path in some cases. WPAD can also be manually enabled on it. However, due to the difference in the implementation details of NetBIOS protocol, this attack does not affect the Mac OS – it would be much cooler otherwise.
0x05 Refrences
[1] Evilgrade
https://github.com/infobyte/evilgrade/
[2] 10 Places to Stick Your UNC Path
https://blog.netspi.com/10-places-to-stick-your-unc-path/
[3] Web Proxy Auto-Discovery Protocol
http://tools.ietf.org/html/draft-ietf-wrec-wpad-01
[4] NetBIOS Over TCP/IP
https://technet.microsoft.com/en-us/library/cc940063.aspx
[5] Disable WINS/NetBT name resolution
https://technet.microsoft.com/en-us/library/cc782733(v=ws.10).aspx
[6] MS99-054, CVE-1999-0858
https://technet.microsoft.com/en-us/library/security/ms99-054.aspx
[7] MS09-008, CVE-2009-0093, CVE-2009-0094
https://technet.microsoft.com/en-us/library/security/ms09-008.aspx
[8] MS12-074, CVE-2012-4776
https://technet.microsoft.com/en-us/library/security/ms12-074.aspx
[9] MS16-063, CVE-2016-3213
https://technet.microsoft.com/en-us/library/security/ms16-063.aspx
[10] MS16-077, CVE-2016-3213, CVE-2016-3236
https://technet.microsoft.com/en-us/library/security/ms16-077.aspx
